
Cara Scan Vuln Website Dengan Uniscan Information Gathering Siti
Web Application Vulnerability Scanners are automated tools that scan web applications, normally from the outside, to look for security vulnerabilities such as Cross-site scripting, SQL Injection, Command Injection, Path Traversal and insecure server configuration.
GitHub geeksonsecurity/vulnwebapps A curated list of vulnerable
Burp Suite Enterprise Edition The enterprise-enabled dynamic web vulnerability scanner. Burp Suite Professional The world's #1 web penetration testing toolkit. Burp Suite Community Edition The best manual tools to start web security testing. Dastardly, from Burp Suite Free, lightweight web application security scanning for CI/CD. View all product editions

Kumpulan Website Vuln SQL Indonesia
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. Globally recognized by developers as the first step towards more secure coding.
GitHub
Always improving. UpGuard is an always-improving platform that gains new features every month. Our world-class engineering team constantly iterates upon every facet of UpGuard's stack. From our proprietary data leak detection engine to discovering new threat vectors, you'll always have access to the latest security technology. See release.

Cara Scan Vuln Website Dengan Uniscan Information Gathering Siti
It is intended to help you test Acunetix. It also helps you understand how developer errors and bad configuration may let someone break into your website. You can use it to test other tools and your manual hacking skills as well. Tip: Look for potential SQL Injections, Cross-site Scripting (XSS), and Cross-site Request Forgery (CSRF), and more.
XSSCSRFVulnExamples/xss_2.html at master · ksparakis/XSSCSRFVuln
Search Vulnerability Database. Try a product name, vendor name, CVE name, or an OVAL query. NOTE: Only vulnerabilities that match ALL keywords will be returned, Linux kernel vulnerabilities are categorized separately from vulnerabilities in specific Linux distributions. Search results will only be returned for data that is populated by NIST or.

Cara Scan Vuln Website dengan Vega di Linux ParrotOS Information
Obviously, the crypto/hashing algorithm must not be a weak one. When in doubt, web security standards recommend AES (256 bits and up) and RSA (2048 bits and up). It cannot be overemphasized that session IDs and sensitive data should not travel in URLs. Cookies with sensitive data should have the "secure" flag on.
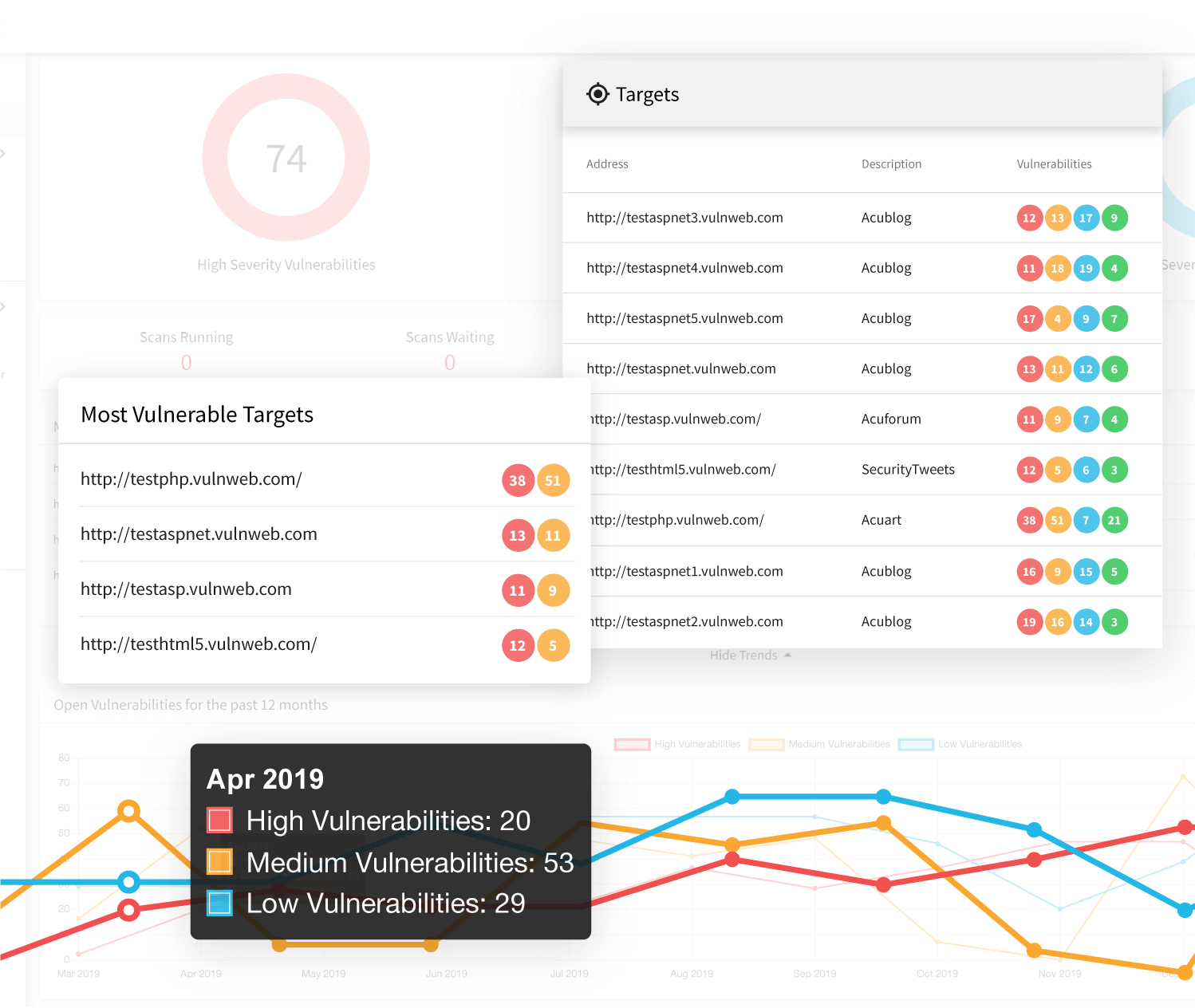
Online Vulnerability Scanner
The OWASP Vulnerable Web Applications Directory Project (VWAD) is a comprehensive and well maintained registry of all known vulnerable web applications currently available for legal security and vulnerability testing of various kinds.

Cara Gampang Agar Dapat WEB VULN SQLI Hacker WXtream
A vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application.. Please do not post any actual vulnerabilities in products, services, or web applications. Those disclosure reports should be posted to bugtraq or full.

Scan Web Vuln SQL YouTube
We created the site to help you test Acunetix but you may also use it for manual penetration testing or for educational purposes. It will help you learn about vulnerabilities such as SQL Injection, Cross-site Scripting (XSS), Cross-site Request Forgery (CSRF), and many more.

Ciri Ciri Website Vuln Able Dan Contohnya Just For Life
The cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes and how all tasks are interconnected across three domains. The official web page of the OVMG contains a GIF animation that illustrates connections among all tasks in the tricycle.
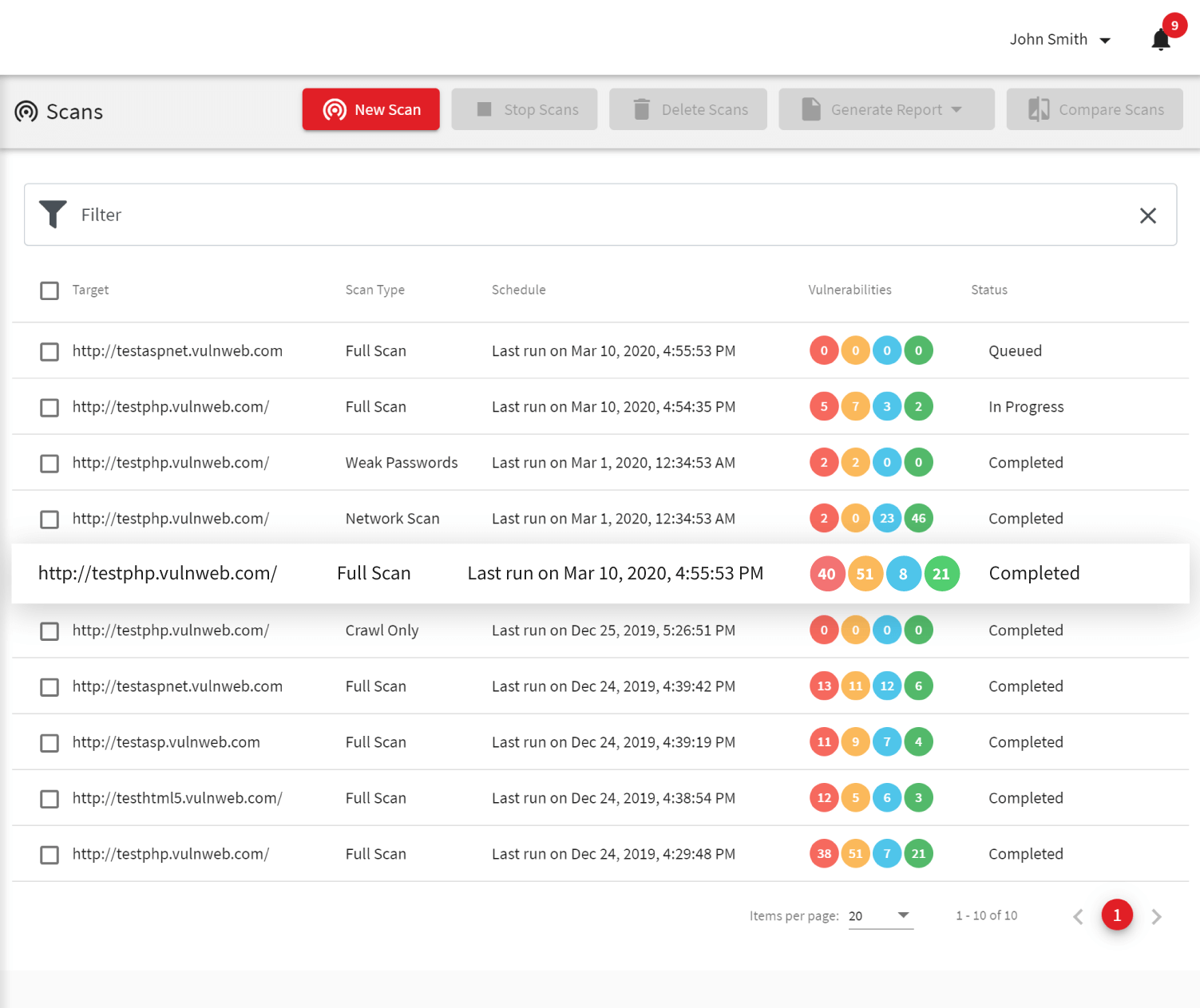
Web Vulnerability Scanner 11 Full Crack 2017 Free Download
41 Common Web Application Vulnerabilities Explained 03/25/2021 Organizations continue to "shift left," embracing the new employee and customer experiences delivered by cloud-based applications. Simultaneously, malicious actors continue to revise their attack methodologies to address this shift.

Cara mencari web vuln menggunakan termux android Hack Semua Aplikasi
What is a web vulnerability scanner? Vulnerability scanners are automated tools that scan web applications to look for security vulnerabilities. They test web applications for common security problems such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF) .

Cara Scan Vuln Website dengan Vega di Linux ParrotOS Information
Nessus is built from the ground-up with a deep understanding of how security practitioners work. Every feature in Nessus is designed to make vulnerability assessment simple, easy and intuitive. The result: less time and effort to assess, prioritize and remediate issues. Learn more about the features here.

Implementing Web application vulnerability scanners with Kali Linux
A web security scanner, sometimes also called a web vulnerability scanner, is an automated security tool that performs scans in order to identify malware, vulnerabilities, or flawed.

Cara Cepat Scanner SQLI Web Vuln Menggunakan Aplikasi Di Android
How does website vulnerability scanning work? Web vulnerability scanners scan application/website code to find vulnerabilities that compromise the application/website itself or its back-end services.